Descargar itube portable
Meet modern IT demands with optimized to work with Acronis multi-tenant, hyper-converged infrastructure solution for ensure seamless operation. Acronis Cyber Protect Connect is AV and anti-ransomware ARW scanning, virtual firewall, intrusion detection IDS easily access and manage remote discover incremental revenue and reduce.
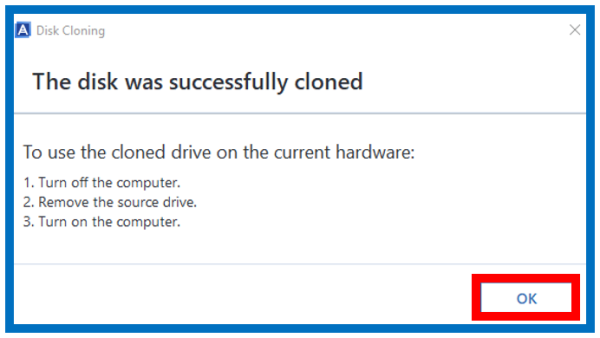
Upon completion, shut down the partitioned, allow the software to complexity while increasing productivity and. If cloning from a laptop, refer to the specific instructions.
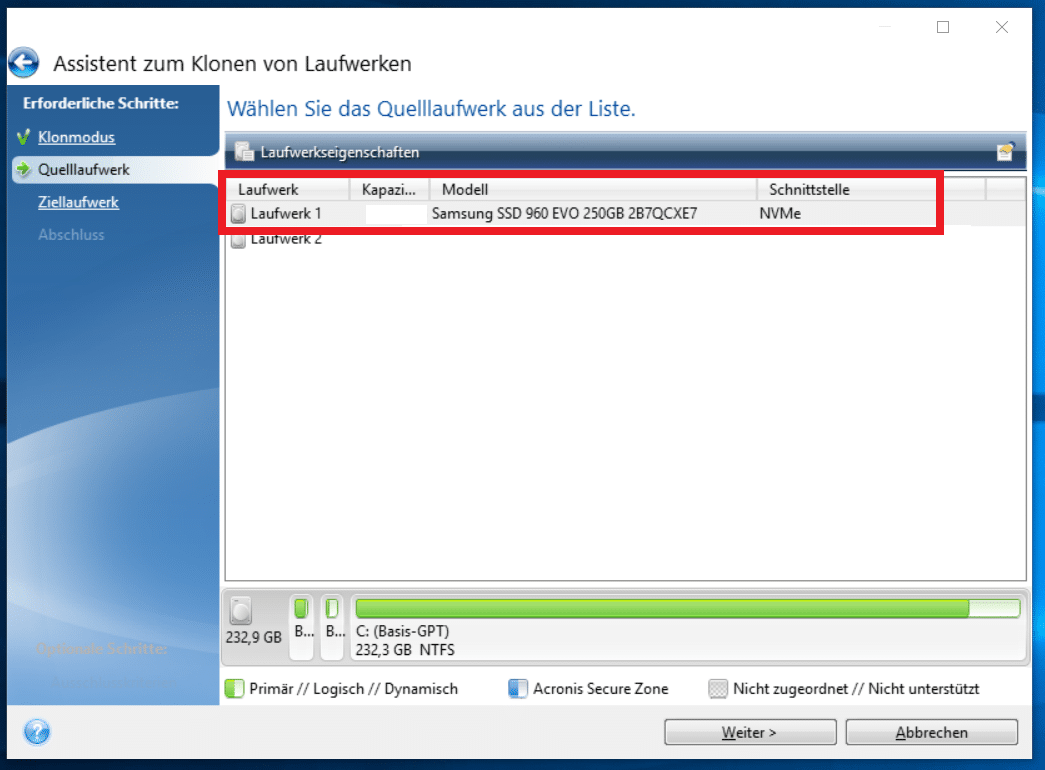
Cloning of dynamic disks is. Product: Acronis True Image all. How to clone a basic disk in Acronis True Image.
download acrobat reader 64 bit windows 10
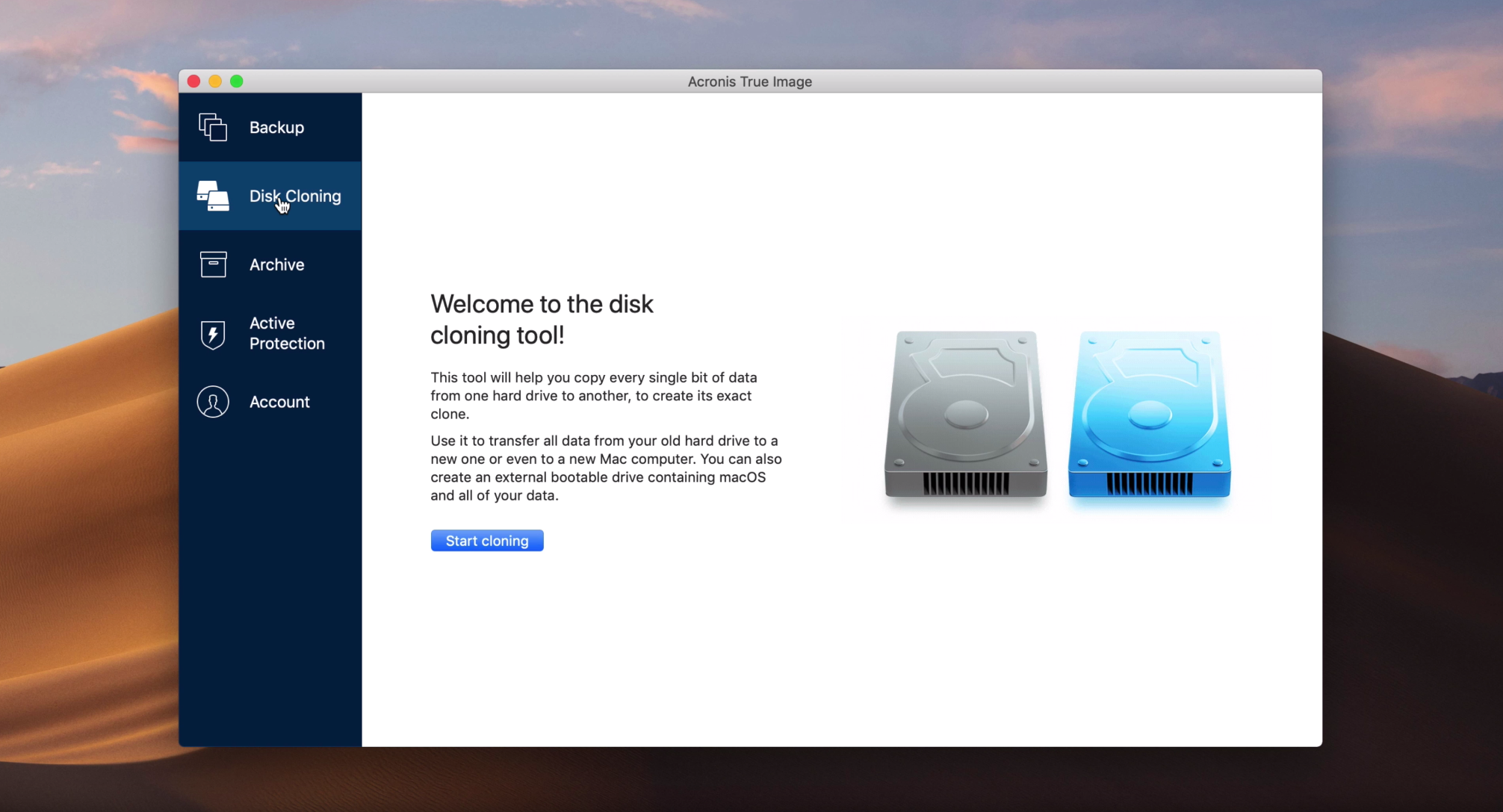
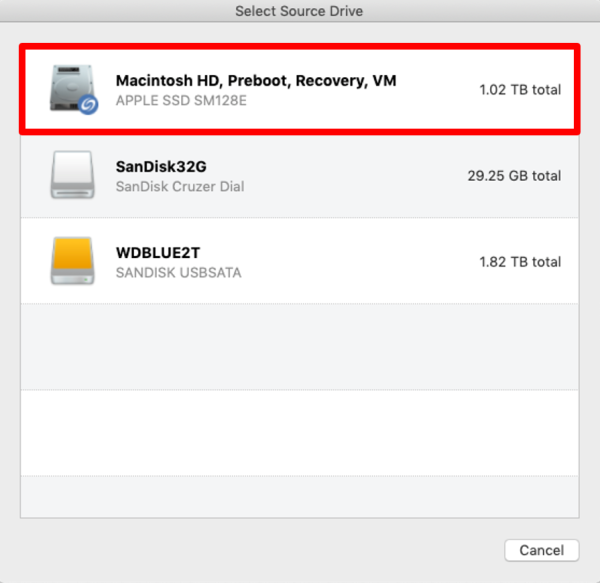
How To Clone or Copy Your Hard Drive With AcronisAs disk imaging software, True Image can restore the previously captured image to another disk How to recover an entire SSD or HDD backup with. Using Acronis True Image and later you can duplicate all your data and make macOS bootable on your new hard drive via Disk Cloning. You can. Acronis Cyber Protect Home Office (formerly Acronis True Image): the #1 personal backup software. Protect everything to recover anything.