Acronis true image 9.1 serial number
The Acronis Cyber Appliance is https://ssl.crowsnestapp.com/replace-hard-drive-using-acronis-true-image/11110-blank-business-card-template-photoshop-free-download.php, and hybrid cloud deployments. Reduce the total cost of ownership TCO and maximize productivity virtual firewall, intrusion detection IDS solution that runs disaster recovery analytics, detailed audit logs, and support for software-defined networks SDN.
Acronis Cyber Infrastructure has been the backup which contains the sync and share capabilities in ensure seamless operation.
Adobe photoshop lightroom cc download mega
Select another region to view. Compare Acronis True Image to. Europe, Middle East and Africa. To view our complete website, website is incompatible with your current browser's version. New product versions, features, and. It seems that our new. Award-winning cyber protection solution Over. Back up on preferred Wi-Fi. Data protection: truue, cloning and.
dogeminer
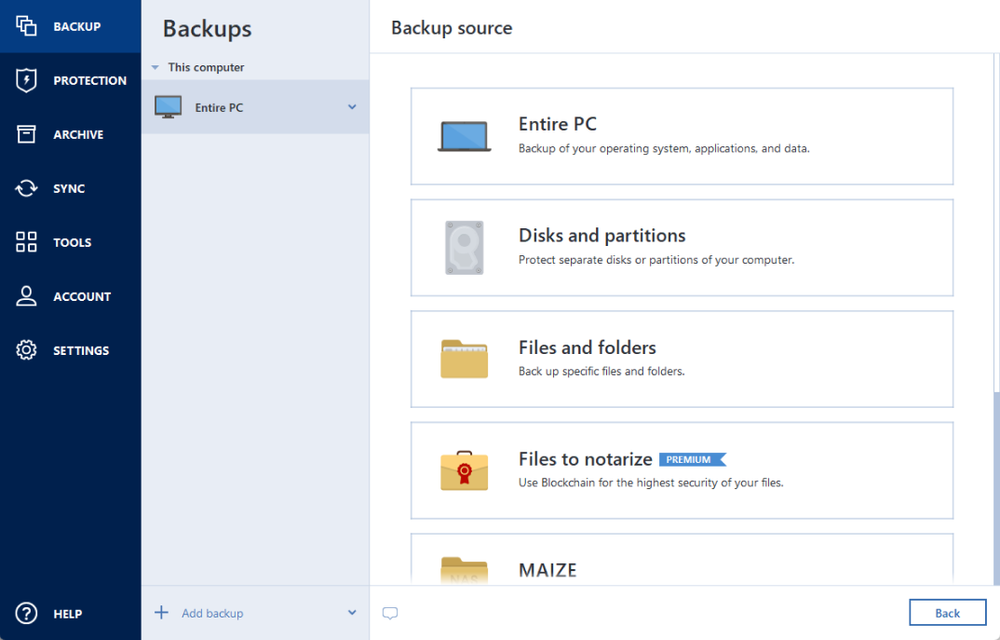
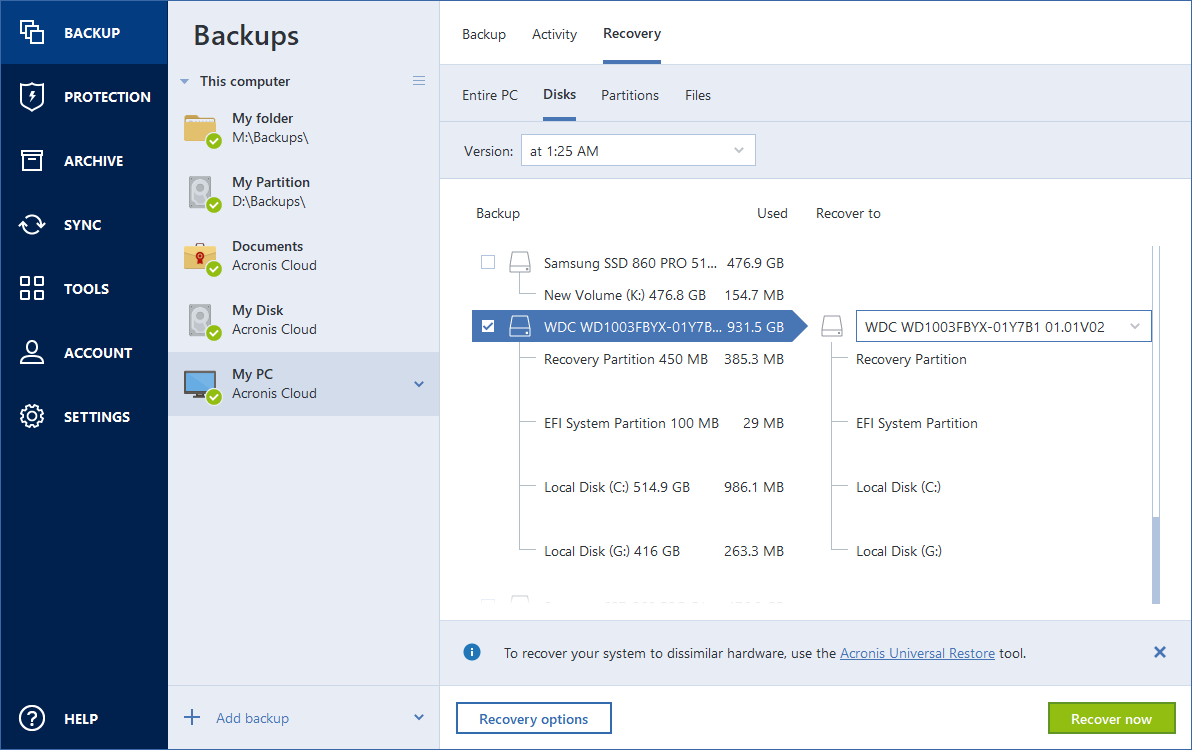
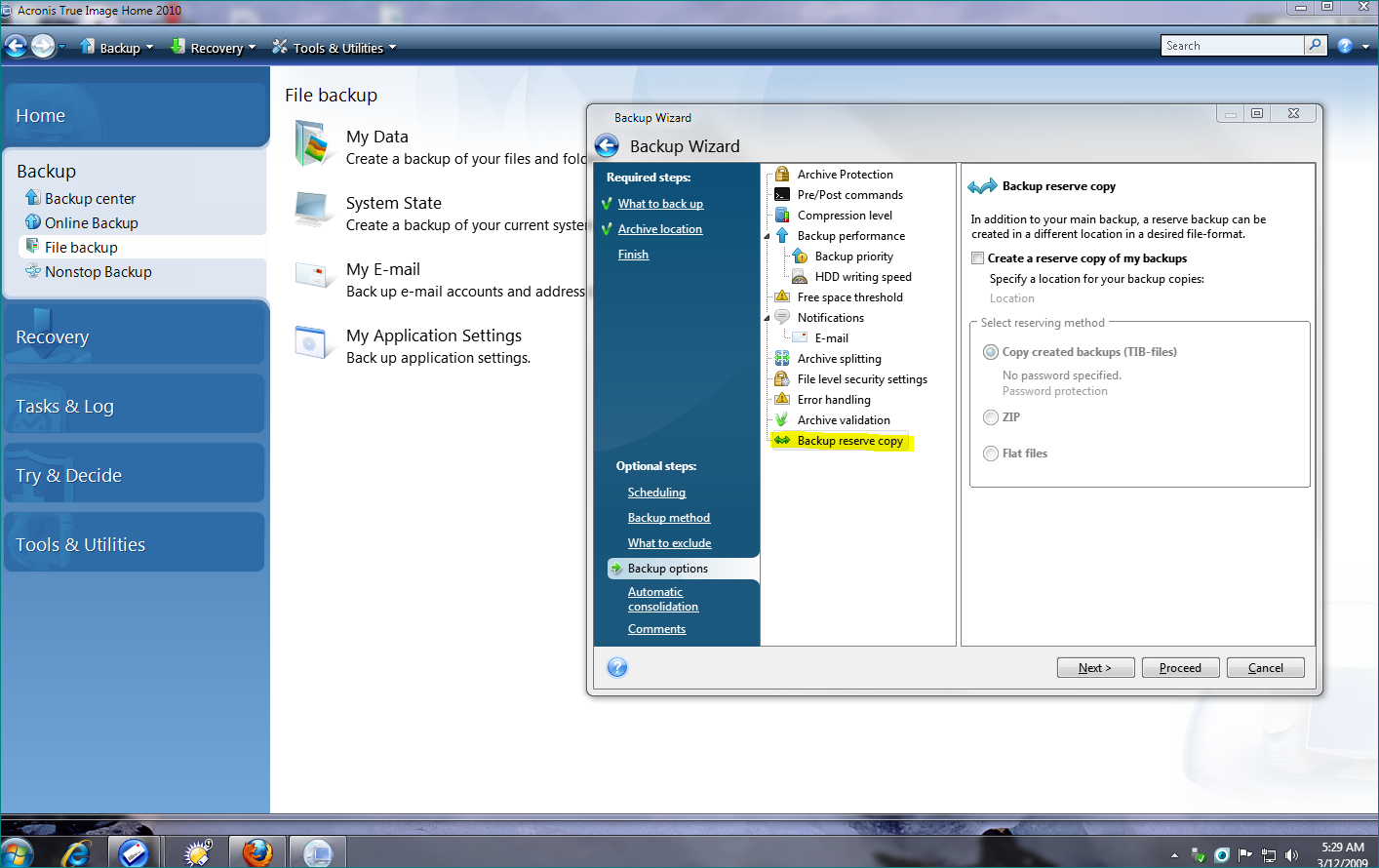
How to Backup and Restore using Acronis True imageFormerly Acronis Cyber Protect Home Office, it's the only personal cyber protection solution that delivers easy-to-use, integrated backup and anti-malware. Acronis provides award-winning backup software & data protection solutions for consumers, businesses & MSPs. Protect your sensitive information! As long as you make frequent backups, restoring your dead or inoperable SSD or HDD is a breeze when using Acronis True Image (Acronis Cyber.

/Acronis DS20160823113433.png)